🔐 Strengthening Cybersecurity with the Essential Eight Framework: What You Need to Know
In today's digital landscape, cyber threats are an ever-present concern for organizations of all sizes. Whether you're a small business owner or managing IT for a large enterprise, the risk of cyberattacks such as ransomware, phishing, and data breaches is real and growing. To combat these threats, the Australian Cyber Security Centre (ACSC) has developed the Essential Eight—a set of eight prioritized mitigation strategies designed to enhance your organization's cybersecurity posture.
In this post, we'll delve into what the Essential Eight is, why it's crucial, and how you can implement it effectively.
What is the Essential Eight?
The Essential Eight is a cybersecurity framework developed by the ACSC to help organizations protect their systems against a range of cyber threats. These strategies are based on the ACSC's extensive experience in producing cyber threat intelligence, responding to cybersecurity incidents, conducting penetration testing, and assisting organizations in implementing effective cybersecurity measures .
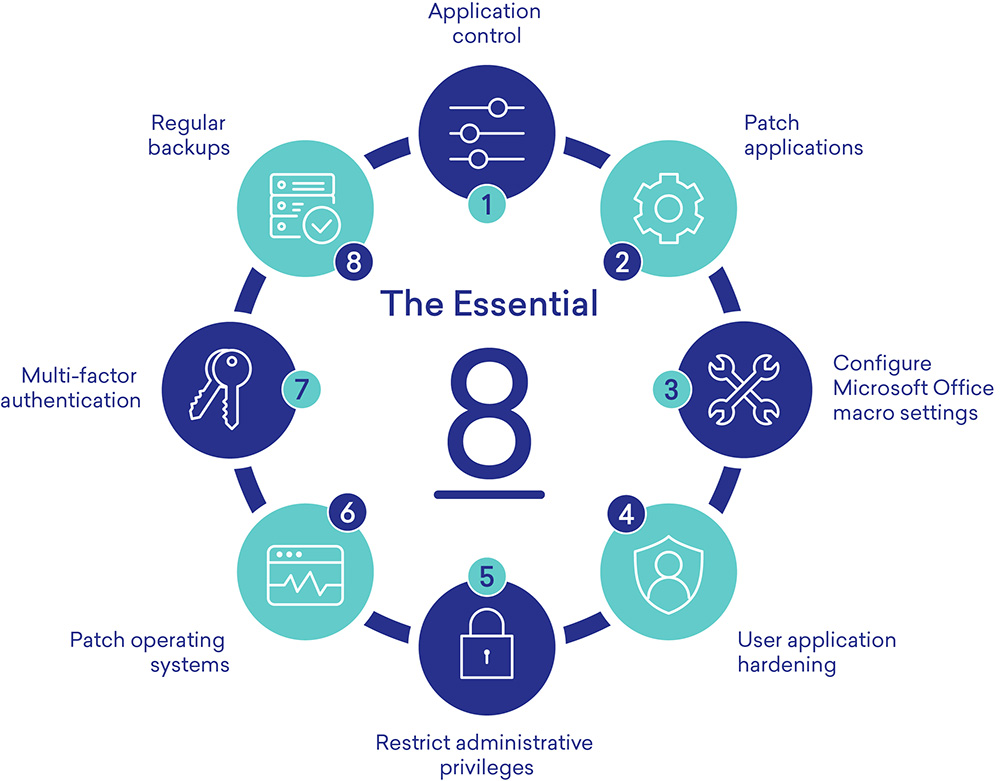
The Essential Eight comprises the following mitigation strategies:
- Application Control: Prevent unauthorized applications from executing.
- Patch Applications: Apply security patches within 48 hours of release.
- Configure Microsoft Office Macro Settings: Disable macros from the internet and only allow vetted macros to run.
- User Application Hardening: Disable unneeded features in web browsers and PDF viewers.
- Restrict Administrative Privileges: Limit and control administrative privileges.
- Patch Operating Systems: Apply security patches within 48 hours of release.
- Multi-Factor Authentication (MFA): Enforce MFA for all remote access and privileged accounts.
- Regular Backups: Backup essential data and systems regularly.
Implementing these strategies makes it significantly harder for adversaries to compromise your systems .
Why the Essential Eight Matters
Implementing the Essential Eight offers several benefits:
- Enhanced Security: Protects against a wide range of cyber threats.
- Compliance: Helps meet regulatory requirements, especially for Australian government entities.
- Cost-Effective: Proactively addressing vulnerabilities can reduce the potential costs of a cyber incident.
- Scalability: Suitable for organizations of all sizes and sectors.
Understanding the Essential Eight Maturity Model
The ACSC provides a Maturity Model to help organizations assess their implementation of the Essential Eight. The model consists of four levels:
- Level 0: No implementation; systems are highly vulnerable.
- Level 1: Basic implementation; provides protection against less sophisticated threats.
- Level 2: Enhanced implementation; protects against more capable adversaries.
- Level 3: Advanced implementation; provides robust protection against advanced threats.
Organizations are encouraged to aim for at least Maturity Level 2 to achieve meaningful protection .
How to Implement the Essential Eight
Implementing the Essential Eight involves the following steps:
- Assess Your Current Security Posture: Evaluate your organization's current cybersecurity measures and identify gaps.
- Prioritize Implementation: Start with high-impact strategies like applying patches and enforcing MFA.
- Develop an Action Plan: Create a roadmap for implementing each of the eight strategies.
-
Monitor and Review: Regularly assess the effectiveness of your implementations and make necessary adjustments.
Final Thoughts
Cybersecurity is an ongoing journey, not a one-time task. By adopting the Essential Eight framework, you can build a robust defense against cyber threats and enhance your organization's resilience. If you need assistance in implementing these strategies or assessing your current cybersecurity posture, contact us today.